SDU IT
Simulated phishing
SDU conducts regular simulations of phishing campaigns against SDU. Read more about how we simulate phishing here.
What is phishing?
Phishing is fake emails, often sent with the purpose of stealing login and payment information or identity theft. Phishing emails are often sent with a fake sender to make it look like the email comes from an acquaintance or colleague. The intention is to gain trust and then trick the user into handing over information. Phishing can also be emails that contain attachments with malicious code that can delete or corrupt data on the computer if opened.
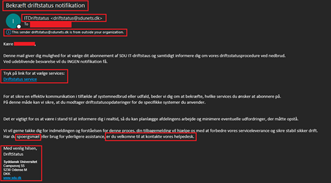
SDU is increasingly receiving malicious emails where our users are tricked into submitting their passwords, among other things. For example, you may be sent an email with SDU's logo, where you have to click on a link to log in to our e-learning platform, confirm account information, etc. The link takes you to a website that is an exact copy of SDU's single sign-on solution. The problem is that it wasn't - and it was only apparent from the browser's URL field.
SDU's example of a simulated phishing attack
How SDU performs simulated phishing
Avoid phishing
Still in doubt?
- Ask a colleague if you are in doubt. Has he or she received the same email? Can you call the sender back? This is especially relevant if you receive an email from "your boss" about paying out large sums of money. This is also known as CEO fraud.
- Call the Service Desk for clarification on 6550 2990 or send an email.
- Your bank or insurance company will never ask you to update your details via email. If in doubt, it's always best to call and ask before entering any information.
Do you have any questions?
The GDPR and Information Security Coordinators are your local contact and advisor for day-to-day data protection and information security at SDU.